ᱵᱚᱴᱱᱮᱴ
"ᱵᱚᱴᱱᱮᱰ" ᱫᱚ ᱦᱩᱭᱩᱜ ᱠᱟᱱᱟ ᱡᱚᱠᱷᱚᱱ ᱢᱤᱫ ᱦᱚᱲ ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱟᱭᱢᱟ ᱤᱱᱴᱟᱨᱱᱮᱴ ᱦᱟᱹᱛᱭᱟᱹᱨ (Device) ᱵᱮᱵᱷᱟᱨ ᱠᱟᱛᱮ ᱱᱟᱱᱟ ᱦᱩᱱᱟᱹᱨ ᱠᱟᱹᱢᱤ ᱠᱟᱱᱟ। ᱵᱚᱴᱱᱮᱰ ᱵᱮᱵᱷᱟᱨ ᱠᱟᱛᱮ ᱰᱤᱥᱴᱨᱤᱵᱤᱭᱩᱴᱮᱰ ᱰᱤᱱᱟᱭᱟᱞ ᱚᱯ ᱥᱟᱨᱵᱷᱤᱥ (DDoS), ᱥᱟᱹᱠᱷᱭᱟᱹᱛ ᱠᱩᱢᱲᱩ, ᱮᱴᱥᱯᱟᱢ ᱵᱷᱮᱡᱟ ᱜᱷᱟᱹᱞ ᱟᱠᱟᱱ ᱵᱮᱵᱷᱟᱨᱤᱭᱟᱹ ᱚᱱᱟ ᱦᱟᱹᱛᱭᱟᱹᱨ ᱛᱮ ᱥᱟᱹᱢᱲᱟᱣ ᱮᱢᱟᱱ ᱠᱚ ᱠᱚᱨᱟᱣ ᱜᱟᱱᱚᱜᱼ ᱟ । ᱵᱚᱴᱱᱮᱰ ᱨᱮᱱ ᱥᱚᱥᱛᱟᱫᱤᱠᱟᱨᱤ ᱠᱟᱢᱟᱰ ᱚᱯ ᱠᱚᱱᱴᱨᱚᱞ (C&C) ᱥᱚᱯᱴᱟᱣᱟᱨ ᱛᱮ ᱚᱱᱟ ᱫᱚ ᱥᱟᱢᱲᱟᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ । ᱵᱚᱰᱱᱮᱴ ᱟᱲᱟᱝ ᱫᱚ ᱦᱮᱡ ᱟᱠᱟᱱᱟ ᱨᱚᱵᱚᱰ ᱠᱷᱚᱱ ᱟᱜ ᱟᱨ ᱱᱮᱴᱣᱟᱨᱠ ᱨᱮᱱᱟᱜ ᱢᱮᱥᱟ ᱠᱟᱛᱮ । ᱟᱲᱟᱝ ᱫᱚ ᱢᱩᱲᱩᱛᱚ ᱱᱤᱛᱤᱵᱟᱪᱚᱠ ᱫᱨᱤᱥᱴᱤᱠᱚᱱ ᱠᱷᱚᱱ ᱟᱜ ᱵᱮᱵᱷᱟᱨ ᱦᱩᱭᱩᱜᱼᱟ।
ᱵᱮᱵᱷᱟᱨ
ᱥᱟᱯᱲᱟᱣᱵᱚᱴᱱᱮᱰ ᱵᱮᱵᱷᱟᱨ ᱦᱩᱭᱩᱜᱼᱟ ᱢᱩᱲᱩᱛᱚ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱨᱮᱭᱟᱜ ᱱᱤᱨᱟᱯᱚᱛᱛᱟ ᱨᱟᱹᱯᱩᱫ ᱠᱟᱛᱮ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱠᱚ ᱥᱟᱢᱲᱟᱣ ᱞᱟᱹᱜᱤᱫ । ᱱᱚᱝᱠᱟ ᱵᱷᱟᱵᱛᱮ ᱟᱭᱢᱟ ᱦᱟᱹᱛᱭᱟᱹᱨ ᱡᱚᱠᱷᱚᱱ ᱠᱳᱱᱳ ᱢᱟᱞᱭᱟᱨ ᱥᱮ ᱠᱷᱚᱛᱤᱠᱚᱨ ᱥᱚᱯᱴᱟᱣᱟᱨ ᱫᱟᱨᱟᱭ ᱛᱮ ᱜᱷᱟᱹᱞ ᱠᱟᱛᱮ ᱮᱴᱟᱜ ᱦᱟᱹᱛᱭᱟᱹᱨ ᱫᱚᱠᱷᱚᱞ ᱠᱟᱛᱮ ᱮᱴᱟᱜ ᱛᱮᱥᱟᱨ ᱥᱮᱫ ᱥᱟᱢᱲᱟᱣ ᱮᱢᱟᱭᱟ ᱩᱱᱚᱠᱛᱚ ᱥᱟᱱᱟᱢ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱢᱤᱢᱤᱫ ᱴᱟᱝ ᱵᱚᱴ ᱦᱩᱭᱩᱜᱼᱟ। ᱚᱱᱟ ᱛᱟᱭᱚᱢ ᱵᱚᱴ ᱨᱮᱱᱟᱜ ᱥᱟᱢᱲᱟᱣ (IRC) ᱟᱨ (Hypertext Transfer Protocol - HTTP) ᱟᱜ ᱢᱚᱛᱛᱮ ᱱᱮᱴᱣᱟᱨᱠ ᱯᱨᱳᱴᱚᱠᱚᱞ ᱵᱮᱵᱷᱟᱨ ᱠᱟᱛᱮ ᱢᱩᱲᱩᱛᱚ ᱥᱟᱭᱵᱟᱨ ᱠᱟᱹᱭᱟᱱ ᱠᱚ ᱚᱱᱟ ᱡᱚᱥᱛᱮ ᱵᱟᱹᱲᱛᱤ ᱵᱚᱴᱱᱮᱰ ᱠᱚ ᱵᱮᱵᱷᱦᱟᱨ ᱮᱫᱟ ।
ᱜᱚᱲᱦᱚᱱ
ᱥᱟᱯᱲᱟᱣᱚᱠᱛᱚ ᱥᱟᱶ ᱥᱟᱶ ᱛᱮ ᱪᱤᱱᱦᱟᱹᱣ ᱞᱟᱹᱜᱤᱫ ᱱᱟᱱᱟ ᱦᱩᱱᱟᱹᱨ ᱦᱚᱨ ᱟᱵᱤᱥᱠᱟᱨ ᱥᱟᱶ ᱥᱟᱶ ᱛᱮ ᱵᱚᱴᱱᱮᱰ ᱨᱮᱱᱟᱜ ᱜᱚᱲᱦᱚᱱ ᱦᱚᱸ ᱵᱚᱫᱚᱞᱚᱜ ᱠᱟᱱᱟ । ᱥᱟᱫᱷᱟᱨᱚᱱᱛᱚ ᱵᱚᱴ ᱯᱨᱳᱜᱨᱟᱢ ᱫᱚ ᱠᱞᱮᱭᱮᱰ ᱦᱤᱥᱟᱹᱵ ᱛᱮ ᱵᱮᱵᱷᱦᱟᱨ ᱦᱩᱭᱩᱜᱼᱟ ᱡᱟᱛᱮ ᱥᱟᱨᱵᱷᱟᱨ ᱥᱟᱞᱟᱜ ᱜᱟᱞᱢᱟᱨᱟᱣ ᱥᱟᱹᱜᱟᱹᱭ ᱠᱚ ᱫᱚ ᱦᱚᱸ ᱫᱟᱲᱮᱭᱟᱜ ᱢᱟ । ᱚᱱᱟ ᱚᱨᱡᱚᱛᱮ ᱵᱚᱴ ᱨᱮᱱᱟᱜ ᱥᱟᱢᱲᱟᱣ (ᱡᱟᱦᱟᱭ ᱵᱚᱴ ᱥᱟᱢᱲᱟᱣ ᱮ ᱠᱟᱱᱟ) । ᱥᱟᱹᱜᱤᱧ ᱠᱷᱚᱱ ᱟᱜ ᱠᱟᱹᱢᱤ ᱠᱚᱭ ᱥᱟᱢᱲᱟᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ । ᱢᱟᱲᱟᱝ ᱨᱮᱱᱟᱜ ᱟᱭᱢᱟ (peer-to-peer) ᱱᱮᱴᱣᱟᱨᱠ ᱛᱟᱞᱟᱛᱮ ᱥᱟᱹᱜᱟᱹᱭ ᱠᱚ ᱫᱚ ᱦᱚᱸ ᱮᱫᱟ। ᱠᱞᱟᱭᱤᱰ ᱥᱟᱨᱵᱷᱟᱨ ᱠᱚᱣᱟᱜ ᱢᱚᱛᱛᱮ (P2P-Peer to Peer) ᱵᱚᱴ ᱯᱨᱳᱜᱨᱟᱢ ᱢᱤᱫ ᱜᱮ ᱠᱟᱹᱢᱤᱭᱟ। ᱚᱱᱟ ᱵᱟᱵᱚᱛᱛᱮ ᱩᱱᱠᱩᱣᱟᱜ ᱟᱨ ᱢᱩᱲᱩᱛ ᱥᱟᱨᱵᱷᱟᱨ ᱨᱮᱱᱟᱜ ᱛᱟᱞᱟᱛᱮ ᱥᱟᱹᱜᱟᱹᱭ ᱵᱟᱝ ᱨᱮᱦᱚ ᱜᱟᱱᱚᱜ ᱜᱮᱭᱟ।
ᱠᱞᱟᱭᱤᱰ ᱥᱟᱨᱵᱷᱟᱨ ᱢᱚᱰᱮᱞ(Client-server model)
ᱥᱟᱯᱲᱟᱣᱤᱱᱴᱟᱨᱱᱮᱴ ᱨᱮᱱᱟᱜ ᱯᱩᱭᱞᱩ ᱥᱮᱫ ᱵᱚᱴᱱᱮᱰ ᱠᱚ ᱞᱠᱟᱭᱤᱰ ᱥᱟᱨᱵᱷᱟᱨ ᱱᱚᱠᱥᱟ ᱩᱱᱩᱥᱟᱨᱮ ᱠᱟᱹᱢᱤ ᱛᱟᱦᱮᱫ ᱠᱚ । ᱥᱟᱫᱷᱟᱨᱚᱱᱛᱚ, ᱱᱚᱣᱟ ᱵᱚᱴ ᱠᱚ ᱫᱚ (IRC-Internet Relay Chat) ᱱᱮᱴᱣᱟᱨᱠ ᱠᱤᱝᱵᱟ ᱳᱭᱮᱵ ᱥᱟᱭᱤᱰ ᱥᱟᱦᱴᱟ ᱨᱮᱱᱟᱜ ᱛᱟᱞᱟᱛᱮ ᱠᱟᱹᱢᱤ ᱠᱟᱱᱟ। ᱜᱷᱟᱹᱞ ᱟᱱ ᱠᱞᱟᱭᱤᱰ ᱨᱮᱱ ᱢᱟᱲᱟᱝ ᱨᱮ ᱠᱷᱚᱱ ᱟᱜ ᱱᱤᱨᱫᱷᱟᱨᱤᱛᱚ ᱢᱤᱫᱴᱟᱝ ᱡᱟᱭᱜᱟ ᱫᱚᱠᱷᱚᱞ ᱠᱟᱛᱮ ᱥᱟᱨᱵᱷᱟᱨ ᱠᱷᱚᱱ ᱟᱜ ᱱᱤᱨᱫᱮᱥ ᱞᱟᱹᱜᱤᱫ ᱛᱟᱜᱤ ᱠᱟᱜᱼᱟ। ᱵᱚᱴ ᱨᱮᱱᱟᱜ ᱥᱟᱢᱲᱟᱣ ᱥᱟᱨᱵᱷᱟᱨ ᱨᱮ ᱩᱱᱤ ᱦᱚᱸ ᱥᱮᱞᱮᱫ ᱫᱟᱲᱮᱭᱟᱜ -ᱟ, ᱡᱟᱦᱟᱭ ᱥᱟᱨᱵᱷᱟᱨ ᱜᱷᱟᱹᱞ ᱟᱠᱟᱱ ᱠᱞᱟᱭᱤᱰ ᱠᱚ ᱟᱲᱟᱜ ᱫᱟᱲᱮᱭᱟ ᱠᱚᱣᱟ । ᱠᱞᱟᱭᱤᱰ ᱨᱮ ᱵᱚᱴ ᱠᱚ ᱩᱫᱩᱜ ᱩᱱᱩᱡᱟᱭᱤ ᱠᱟᱹᱢᱤ ᱠᱟᱛᱮ ᱥᱟᱹᱠᱷᱭᱟᱹᱛ ᱥᱟᱨᱵᱷᱟᱨ ᱨᱮ ᱵᱷᱮᱡᱟᱭᱟ।
IRC ᱵᱚᱴᱱᱮᱰ ᱠᱚ ᱠᱷᱮᱛᱨᱚ ᱨᱮ, ᱜᱷᱟᱹᱞ ᱟᱠᱟᱱ ᱠᱞᱟᱭᱤᱰ ᱡᱟᱦᱟᱭ ᱜᱷᱟᱹᱞ IRC ᱥᱟᱶ ᱥᱮᱞᱮᱫ ᱦᱩᱭᱩᱜᱼᱟ ᱟᱨ ᱢᱟᱲᱟᱝ ᱠᱷᱚᱱ ᱟᱜ ᱵᱚᱴ ᱥᱟᱢᱲᱟᱣ ᱛᱮᱭᱟᱨ ᱟᱠᱟᱱ ᱪᱮᱱᱮᱞ ᱥᱟᱶ ᱥᱮᱞᱮᱫ -ᱟ । ᱱᱚᱣᱟ ᱠᱷᱮᱛᱨᱚ ᱨᱮ IRC ᱛᱟᱞᱟᱛᱮ ᱪᱮᱱᱮᱞ ᱨᱮ ᱱᱤᱨᱫᱮᱥ ᱵᱷᱮᱡᱟᱭᱟ ᱟᱠᱟ ᱠᱚ ᱛᱟᱦᱮᱱᱟ । ᱥᱟᱱᱟᱢ ᱠᱞᱟᱭᱤᱰ ᱠᱚ ᱱᱤᱨᱫᱮᱥ ᱠᱚ ᱢᱟᱱᱟᱣ ᱵᱟᱰᱟᱣ ᱠᱟᱛᱮ ᱪᱟᱞᱟᱣ ᱦᱩᱭᱩᱜᱼᱟ, ᱟᱨ ᱩᱱᱤ ᱟᱡᱟᱜ ᱢᱚᱛᱟ ᱢᱚᱛᱛᱮ IRC ᱪᱮᱱᱮᱞ ᱨᱮ ᱥᱟᱹᱠᱷᱭᱟᱹᱛ ᱵᱷᱮᱡᱟᱭᱟ ᱠᱚ ।
ᱟᱹᱰᱤ ᱢᱟᱲᱟᱝ ᱠᱷᱚᱱ ᱟᱜ IRC ᱜᱟᱞᱢᱟᱨᱟᱣ ᱟᱨ ᱩᱱᱤ ᱭᱟᱜ ᱯᱨᱳᱴᱳᱠᱚᱞ ᱠᱟᱨᱚᱱᱛᱮ 'ᱠᱟᱢᱟᱰ ᱚᱯ ᱠᱚᱱᱴᱨᱚᱞ ' ᱵᱷᱤᱛᱤᱨ ᱨᱮ ᱛᱟᱦᱮᱱᱟ। ᱵᱚᱴ ᱱᱤᱭᱚᱱᱛᱚᱨᱚᱠ ᱟᱡᱛᱮ ᱟᱭᱟᱨᱥᱤ ᱪᱮᱱᱮᱞ ᱛᱮᱭᱟᱨ ᱠᱟᱛᱮ ᱡᱟᱛᱮ ᱜᱷᱟᱹᱞ ᱟᱠᱟᱱ ᱠᱞᱟᱭᱤᱰ ᱠᱚ ᱥᱮᱞᱮᱫ ᱫᱟᱲᱮᱭᱟ ᱠᱚᱣᱟ । ᱮᱢᱚᱱ ᱠᱤ ᱱᱤᱭᱚᱱᱛᱚᱨᱚᱠ ᱵᱚᱴ ᱠᱚ ᱱᱤᱨᱫᱮᱥ ᱵᱷᱮᱡᱟ ᱠᱟᱛᱮ ᱪᱮᱱᱮᱞ ᱨᱮᱱᱟᱜ ᱟᱨᱩ ᱯᱷᱮᱨᱟᱣ ᱫᱟᱲᱮᱭᱟ। ᱡᱮᱞᱮᱠᱟ :
:herder!herder@example.com TOPIC #channel ddos www.victim.com
ᱱᱚᱣᱟ ᱠᱟᱛᱷᱟ ᱫᱚ ᱵᱚᱴ ᱱᱤᱭᱚᱱᱛᱚᱨᱚᱠ ᱡᱩᱫᱤ ᱵᱷᱮᱡᱟ ᱢᱚᱱᱮ ᱦᱩᱭᱩᱜ ᱛᱟᱭᱟ #channel ᱨᱮᱱ ᱥᱟᱱᱟᱢ ᱜᱷᱟᱹᱞ ᱟᱠᱟᱱ ᱠᱞᱟᱭᱤᱰ ᱠᱚ www.victim.com ᱨᱮ DDoS ᱜᱷᱟᱹᱞ ᱪᱟᱞᱟᱣ ᱞᱟᱹᱜᱤᱫ ᱟᱨᱡᱤ ᱮᱢᱟ ᱠᱚᱣᱟ । ᱵᱚᱴ ᱠᱞᱟᱭᱤᱰ ᱠᱚ ᱦᱩᱞᱥᱟᱹᱭ ᱮᱛᱚᱦᱚᱵ ᱞᱮᱠᱷᱟᱱ ᱯᱤᱨᱛᱤ ᱠᱟᱛᱷᱟ ᱨᱮ ᱱᱚᱝᱠᱟᱱ ᱠᱟᱛᱷᱟ ᱵᱷᱮᱡᱟ ᱫᱟᱲᱮᱭᱟ -
:bot1!bot1@compromised.net PRIVMSG #channel I am ddosing www.victim.com
ᱟᱭᱟᱨᱥᱤ ᱵᱮᱵᱷᱦᱟᱨ ᱨᱮ ᱢᱤᱫᱴᱟᱝ ᱟᱱᱟᱴ ᱜᱮ ᱵᱚᱴ ᱦᱤᱥᱟᱹᱵ ᱛᱮ ᱵᱮᱵᱷᱦᱟᱨ ᱞᱟᱹᱜᱤᱫ ᱡᱷᱚᱛᱚ ᱵᱚᱴ ᱠᱞᱟᱭᱤᱰ ᱠᱚ ᱩᱱᱠᱩᱣᱟᱜ ᱥᱟᱨᱵᱷᱟᱨ, ᱯᱳᱥᱴ ᱟᱨ ᱪᱮᱱᱮᱞ ᱵᱟᱵᱚᱛᱛᱮ ᱚᱵᱚᱥᱥᱚᱭ ᱵᱟᱰᱟᱭ ᱛᱟᱦᱮ ᱫᱚᱨᱠᱟᱨ। ᱢᱟᱞᱣᱟᱨ ᱵᱤᱨᱩᱫᱤᱭᱟᱹ ᱠᱚ (Anti-malware) ᱜᱷᱟᱶᱛᱟ ᱠᱚ ᱵᱟᱰᱟᱭ ᱞᱮᱠᱷᱟᱱ ᱪᱮᱱᱮᱞ ᱠᱚ ᱢᱩᱪᱟᱹᱫ ᱫᱟᱲᱮᱭᱟᱜ -ᱟ, ᱡᱟᱛᱮ ᱵᱚᱴᱱᱮᱴ ᱦᱩᱞᱥᱟᱹᱭ ᱠᱷᱚᱱ ᱟᱜ ᱵᱤᱨᱩᱫᱤᱭᱟᱹ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ। ᱡᱩᱫᱤ ᱱᱚᱝᱠᱟ ᱦᱩᱭᱩᱜᱼᱟ, ᱛᱟᱭ ᱠᱞᱟᱭᱤᱰ ᱠᱚ ᱜᱷᱟᱹᱞ ᱟᱠᱟᱱ ᱦᱟᱞᱚᱛ ᱨᱮ ᱛᱟᱦᱮᱱᱟᱠᱚ । ᱩᱱᱠᱩ ᱫᱚ ᱚᱠᱟ ᱱᱤᱨᱫᱮᱥ ᱦᱚᱸ ᱵᱟᱝ ᱠᱚ ᱦᱟᱛᱟᱣᱟ ᱫᱟᱲᱮᱭᱟᱜ ᱠᱟᱱᱟ, ᱚᱱᱟ ᱠᱷᱮᱛᱨᱚ ᱨᱮ ᱥᱩᱯᱛᱚ ᱦᱟᱞᱚᱛ ᱨᱮ ᱠᱞᱟᱭᱤᱰ ᱠᱚ ᱛᱟᱦᱮᱱᱟᱠᱚ । ᱱᱚᱣᱟ ᱟᱱᱟᱴ ᱥᱟᱞᱦᱮ ᱨᱮ, ᱢᱤᱫᱴᱟᱝ ᱵᱚᱴᱱᱮᱴ ᱨᱮᱱᱟᱜ ᱟᱭᱟᱨᱥᱤ ᱥᱟᱨᱵᱷᱟᱨ ᱥᱮ ᱟᱭᱢᱟ ᱪᱮᱱᱮᱞ ᱛᱟᱦᱮ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ। ᱡᱩᱫᱤ ᱡᱟᱦᱟ ᱢᱤᱫᱴᱟᱝ ᱥᱟᱨᱵᱷᱟᱨ ᱥᱮ ᱪᱮᱱᱮᱞ ᱢᱩᱪᱟᱹᱫ ᱦᱩᱭᱩᱜᱼᱟ,ᱚᱱᱟ ᱦᱟᱞᱚᱛ ᱨᱮ ᱵᱚᱴ ᱠᱚ ᱮᱴᱟᱜ ᱟᱨ ᱢᱤᱫᱴᱟᱝ ᱥᱟᱨᱵᱷᱟᱨ ᱥᱮ ᱪᱮᱱᱮᱞ ᱨᱮᱱᱟᱜ ᱴᱷᱟᱶ ᱵᱚᱫᱚᱞ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ।
ᱛᱟᱨᱯᱚᱨᱮ ᱦᱚᱸ ᱟᱭᱟᱨᱥᱤ ᱪᱚᱞᱟᱠᱟᱞᱤᱱ ᱱᱚᱡᱚᱨ ᱫᱚ ᱦᱚᱸ ᱠᱟᱛᱮ ᱪᱮᱱᱮᱞ ᱥᱮ ᱥᱟᱨᱵᱷᱟᱨ ᱯᱟᱡᱟ ᱧᱟᱢ ᱠᱟᱛᱮ ᱚᱱᱟ ᱠᱚ ᱢᱩᱪᱟᱹᱫ ᱠᱚᱨᱟᱣ ᱥᱟᱢᱵᱷᱚᱵ। ᱟᱭᱢᱟ ᱥᱮᱬᱟ ᱵᱚᱴᱱᱮᱴ ᱟᱭᱟᱨᱥᱤ ᱵᱚᱫᱚᱞ ᱛᱮ ᱰᱚᱢᱮᱱ (domain) ᱵᱮᱵᱷᱦᱟᱨ ᱛᱟᱦᱮᱫ ᱠᱚ।
ᱚᱱᱟ ᱠᱚ ᱢᱩᱬᱩᱛᱚ ᱵᱮᱜᱷᱚᱴᱚᱱ ᱦᱚᱥᱴᱤᱝ ᱥᱟᱨᱵᱷᱤᱥᱨᱮ ᱡᱟᱭᱜᱟ ᱦᱟᱛᱟᱣᱟ ।
(Peer-to-Peer)
ᱥᱟᱯᱲᱟᱣᱟᱭᱟᱨᱥᱤ ᱵᱚᱴ ᱠᱚ ᱯᱟᱡᱟ ᱧᱟᱢ ᱜᱷᱟᱹᱞ ᱟᱠᱟᱱ ᱞᱟᱹᱜᱤᱫ ᱵᱚᱴ ᱱᱤᱭᱚᱱᱛᱚᱨᱚᱠ ᱯᱮᱭᱟᱨᱼᱴᱩᱼᱯᱮᱭᱟᱨ ᱱᱮᱴᱣᱟᱨᱠ ᱢᱟᱞᱣᱟᱨ ᱯᱟᱥᱱᱟᱣ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ। ᱚᱱᱟ ᱠᱚ ᱵᱚᱴ ᱠᱚ ᱰᱤᱡᱤᱴᱮᱞ ᱥᱩᱦᱤ ᱵᱮᱵᱷᱦᱟᱨ ᱠᱟᱛᱮ ᱡᱟᱛᱮ ᱯᱨᱟᱭᱵᱷᱮᱰ ᱠᱤ (Private Key) ᱵᱟᱵᱚᱛᱛᱮ ᱚᱱᱟ ᱠᱚ ᱱᱤᱭᱚᱱᱛᱚᱨᱚᱠ ᱵᱟᱭ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ। ᱚᱱᱟ ᱞᱮᱠᱟᱱᱟᱜ ᱵᱚᱴᱱᱮᱴ ᱨᱮᱱᱟᱜ ᱫᱟᱹᱭᱠᱟᱹ ᱦᱩᱭᱩᱜ ᱠᱟᱱᱟ - Gameover ZeuS ᱟᱨ ZeroAccess ᱵᱚᱴᱱᱮᱴ ᱨᱮ। ᱛᱩᱞᱟᱹ ᱡᱚᱠᱷᱟ ᱱᱟᱣᱟ ᱵᱚᱴᱱᱮᱴ ᱠᱚ ᱯᱮᱭᱟᱨᱼᱴᱩᱼᱯᱮᱭᱟᱨ ᱱᱮᱴᱣᱟᱨᱠ ᱯᱩᱨᱟᱹᱫᱚᱢᱮ ᱠᱟᱹᱢᱤ ᱫᱟᱲᱮᱭᱟᱜᱼᱟ। ᱛᱟᱞᱢᱟ ᱞᱮᱠᱟᱛᱮ ᱡᱟᱦᱟ ᱥᱟᱨᱵᱷᱟᱨ ᱨᱮ ᱥᱟᱶᱛᱮ ᱡᱳᱜᱟᱡᱩᱜ ᱵᱟᱵᱚᱛᱛᱮ ᱯᱮᱭᱟᱨᱼᱴᱩᱼᱯᱮᱭᱟᱨ ᱢᱤᱫ ᱥᱟᱶᱛᱮ ᱠᱞᱟᱭᱤᱰ ᱨᱮ ᱟᱨ ᱟᱫᱮᱥ ᱮᱢᱚᱜᱤᱭᱟᱹ ᱞᱮᱠᱟᱛᱮ ᱦᱤᱥᱟᱹᱵ ᱛᱮ ᱠᱟᱹᱢᱤᱭᱟ । ᱚᱱᱟ ᱵᱚᱫᱚᱞ ᱛᱮ ᱛᱟᱞᱢᱟ ᱥᱟᱨᱵᱷᱟᱨ ᱴᱮᱦᱟᱰ ᱵᱚᱴᱱᱮᱴ ᱛᱩᱞᱟᱹᱡᱚᱠᱷᱟ ᱨᱮᱱᱟᱜ ᱵᱮᱨᱛᱷᱚᱛᱟ ᱥᱚᱝ ᱠᱚᱢ ᱦᱩᱭᱩᱜᱼᱟ। ᱢᱤᱫ ᱞᱮᱠᱟᱱᱟᱜ ᱮᱴᱟᱜ ᱜᱷᱟᱞ ᱢᱮᱥᱤᱱ ᱨᱮᱱᱟᱜ ᱯᱟᱡᱟᱛᱮ ᱵᱚᱴ ᱯᱳᱱᱥᱮᱫ ᱵᱷᱮᱜᱟᱨ ᱵᱷᱮᱜᱟᱨ IP address ᱯᱟᱡᱟ ᱨᱮ ᱛᱟᱦᱮᱱᱟ ᱡᱟᱦᱟ ᱛᱤᱱ ᱫᱷᱟᱵᱤᱡ ᱚᱱᱠᱟᱱᱟᱜ ᱵᱟᱭ ᱯᱟᱡᱟ ᱧᱟᱢᱟ । ᱛᱟᱭᱚᱢ ᱵᱚᱴ ᱩᱱᱚᱠᱛᱚ ᱱᱟᱱᱟ ᱦᱩᱱᱟᱹᱨ ᱵᱷᱮᱜᱟᱨ ᱥᱟᱹᱠᱷᱭᱟᱹᱛ ᱡᱮᱞᱮᱠᱟ - ᱥᱚᱯᱴᱟᱣᱟᱨ ᱵᱷᱟᱨᱥᱚᱱ ᱥᱮ ᱩᱱᱠᱩᱣᱟᱜ ᱵᱚᱴ ᱛᱟᱞᱤᱠᱟ ᱮᱢᱟᱱ ᱯᱩᱭᱞᱩ ᱵᱚᱴ ᱥᱚᱨ ᱨᱮ ᱵᱷᱮᱡᱟ ᱟᱠᱟᱱ ᱛᱟᱦᱮᱱᱟ। ᱛᱟᱭᱚᱢ ᱟᱠᱟᱱ ᱵᱚᱴ ᱠᱚ ᱞᱟᱦᱟ ᱞᱟᱹᱜᱤᱫ ᱦᱟᱞᱜᱟᱛᱟ ᱞᱟᱹᱠᱛᱤᱜᱼᱟ ।
ᱵᱚᱴᱱᱮᱴ ᱨᱮᱱᱟᱜ ᱢᱳᱞᱤᱠ ᱩᱛᱯᱟᱫᱟᱱ ᱥᱩᱢᱮᱫ
ᱥᱟᱯᱲᱟᱣᱵᱚᱴᱱᱮᱴ ᱨᱮ ᱱᱟᱱᱟ ᱦᱩᱱᱟᱹᱨ ᱩᱛᱯᱟᱫᱟᱱ ᱥᱩᱢᱮᱫ ᱢᱮᱱᱟᱭᱟ। ᱚᱱᱟ ᱢᱩᱫ ᱨᱮ ᱠᱤᱪᱷᱩ ᱞᱟᱛᱟᱨ ᱨᱮ ᱮᱢ ᱟᱠᱟᱱ ᱵᱚᱨᱱᱟ ᱠᱚ ᱦᱩᱭᱩᱜ ᱠᱟᱱᱟ -
ᱠᱟᱢᱟᱰ ᱚᱯ ᱠᱚᱱᱴᱨᱚᱞ
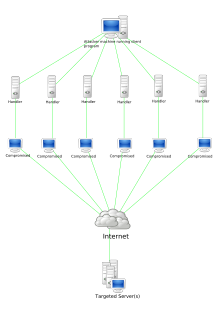
ᱥᱟᱯᱲᱟᱣᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱥᱟᱶ ᱥᱤᱠᱤᱭᱩᱨᱤᱴᱤ ᱵᱷᱟᱵᱛᱮ, ᱠᱟᱢᱟᱰ ᱚᱯ ᱠᱚᱱᱴᱨᱚᱞ ᱠᱟᱴᱷᱟᱢᱚ ᱥᱟᱨᱵᱷᱟᱨ ᱟᱨ ᱮᱴᱟᱜ ᱯᱨᱳᱡᱩᱠᱛᱤ ᱜᱚᱲᱦᱚᱱ ᱥᱟᱶ ᱡᱟᱦᱟ ᱩᱫᱮᱥᱚᱥᱚ ᱢᱟᱞᱣᱟᱨ ᱛᱚᱛᱷᱟ ᱵᱚᱴᱱᱮᱴ ᱨᱮᱱᱟᱜ ᱥᱟᱢᱲᱟᱣ। ᱠᱟᱢᱟᱰ ᱚᱯ ᱠᱚᱱᱴᱨᱚᱞ ᱦᱩᱭᱩᱜ ᱠᱟᱱᱟ ᱢᱟᱞᱣᱟᱨ ᱚᱯᱟᱨᱮᱴᱟᱨ ᱫᱟᱨᱟ ᱛᱮ ᱥᱟᱢᱲᱟᱣ ᱟᱨ ᱩᱱᱠᱩ ᱟᱯᱱᱟᱨ ᱦᱟᱰᱣᱟᱨ ᱨᱮᱱᱟᱜ ᱛᱟᱞᱟᱛᱮ ᱥᱟᱢᱲᱟᱣ ᱠᱟᱛᱮ ᱫᱚᱦᱚᱭᱟ। (Fast-flux DNS) ᱛᱮ ᱠᱚᱱᱴᱨᱚᱞ ᱥᱟᱨᱵᱷᱟᱨ ᱯᱟᱡᱟ ᱧᱟᱢ ᱠᱟᱛᱮ ᱠᱷᱟᱨᱟᱯ ᱠᱚᱨᱟᱣ ᱥᱚᱢᱵᱷᱚᱵ, ᱡᱩᱫᱤᱭᱚ ᱥᱟᱨᱟᱫᱤᱱ ᱟᱹᱨᱩ ᱯᱷᱮᱨᱟᱜ ᱠᱟᱱᱟ । ᱠᱚᱱᱴᱨᱚᱞ ᱥᱟᱨᱵᱷᱟᱨ ᱫᱤᱱᱟᱹᱢ ᱧᱩᱛᱩᱢ ᱩᱛᱱᱟᱹᱣ ᱮᱞᱜᱚᱨᱤᱫᱮᱢ ᱵᱮᱵᱷᱦᱟᱨ ᱠᱟᱛᱮ ᱢᱤᱫ DNS ᱠᱷᱚᱱ ᱟᱜ ᱟᱨ ᱢᱤᱫᱴᱟᱝ DNS ᱨᱮ ᱟᱹᱨᱩ ᱫᱟᱲᱮᱭᱟᱜᱟ। ᱠᱤᱪᱷᱩ ᱠᱷᱮᱛᱨᱚ ᱨᱮ, ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱨᱩᱠᱷᱤᱭᱟᱹ ᱵᱤᱥᱮᱥᱚᱠᱠᱚ ᱥᱚᱯᱷᱚᱞ ᱵᱷᱟᱵᱛᱮ ᱢᱟᱞᱣᱟᱨ ᱠᱟᱢᱟᱰ ᱮᱰ ᱠᱚᱱᱴᱨᱚᱞ ᱱᱮᱴᱣᱟᱨᱠ ᱨᱟᱹᱯᱩᱫ ᱞᱟᱹᱜᱤᱫ ᱠᱚ ᱥᱚᱠᱷᱚᱢ ᱟᱠᱟᱱᱟ। ᱚᱱᱟ ᱢᱤᱫ ᱨᱮ ᱢᱮᱱᱟᱜᱟ - ᱥᱟᱨᱵᱷᱟᱨ ᱟᱴᱚᱠ ᱠᱚᱨᱟᱣ, ᱥᱟᱨᱵᱷᱟᱨ ᱤᱱᱴᱟᱨᱱᱮᱰ ᱠᱷᱚᱱ ᱟᱜ ᱵᱷᱮᱜᱟᱨ ᱠᱚᱨᱟᱣ, ᱡᱟᱦᱟ ᱰᱚᱢᱮᱱ ᱫᱟᱨᱟᱭ ᱛᱮ ᱢᱟᱞᱣᱟᱨ ᱨᱮᱱᱟᱜ ᱠᱟᱢᱟᱰ ᱮᱰ ᱠᱚᱱᱴᱨᱚᱞ ᱥᱟᱨᱵᱷᱟᱨ ᱨᱮ ᱥᱟᱹᱜᱟᱹᱭᱟ ᱚᱱᱟ ᱠᱚ ᱵᱟᱛᱤᱞ ᱠᱚᱨᱟᱣ ᱵᱟᱝᱠᱷᱟᱱ ᱠᱟᱢᱟᱰ ᱮᱰ ᱠᱚᱱᱴᱨᱚᱞ ᱱᱮᱴᱣᱟᱨᱠ ᱜᱮ ᱧᱮᱞ ᱦᱩᱭᱩᱜ । ᱚᱱᱟ ᱨᱮᱱᱟᱜ ᱚᱨᱡᱚ ᱥᱩᱨᱩᱯ,ᱠᱟᱢᱟᱰ ᱮᱰ ᱠᱚᱱᱴᱨᱚᱞ ᱪᱟᱪᱞᱟᱣᱤᱭᱟᱹ ᱠᱚ ᱠᱳᱥᱚᱞ ᱵᱚᱫᱚᱞ ᱟᱠᱟ ᱢᱮᱱᱟᱜ ᱠᱚᱣᱟ। ᱡᱮᱞᱮᱠᱟ -ᱠᱟᱢᱟᱰ ᱮᱰ ᱠᱚᱱᱴᱨᱚᱞ ᱱᱮᱴᱣᱟᱨᱠ ᱪᱟᱞᱟᱜ ᱱᱟᱯᱟᱭ IRC ᱥᱮ (Tor) ᱠᱟᱴᱷᱟᱢᱚ ᱩᱠᱩ ᱨᱮ ᱪᱟᱞᱟᱣ ᱦᱩᱭᱩᱜ -ᱟ, ᱯᱮᱭᱟᱨᱼᱴᱩᱼᱯᱮᱭᱟᱨ ᱱᱮᱴᱣᱟᱨᱠ ᱟᱭᱢᱟ ᱪᱟᱪᱞᱟᱣᱤᱭᱟᱹ ᱠᱚ ᱡᱟᱛᱮ ᱱᱤᱨᱫᱤᱥᱴᱚ ᱥᱟᱨᱵᱷᱟᱨ ᱪᱮᱛᱟᱱ ᱨᱮ ᱴᱮᱦᱟᱰ ᱠᱚᱢᱚᱜ ᱢᱟ ᱟᱨ ᱯᱟᱵᱞᱤᱠ ᱠᱤ ᱮᱱᱠᱨᱤᱯᱥᱚᱱ ᱵᱮᱵᱷᱦᱟᱨ ᱛᱟᱞᱟ ᱛᱮ ᱱᱮᱴᱣᱟᱨᱠ ᱫᱚᱠᱷᱚᱞ ᱫᱟᱨᱟᱢ ᱢᱮ ।
ᱡᱚᱢᱵᱤ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ(Zombie computer)
ᱥᱟᱯᱲᱟᱣᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱥᱟᱭᱤᱱᱥ ᱨᱮ,ᱡᱚᱢᱵᱤ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱞᱟᱹᱭᱛᱮ ᱮᱢᱚᱱ ᱢᱤᱫ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱵᱩᱡᱷᱟᱹᱜ -ᱟ ᱡᱟᱦᱟᱭ ᱤᱱᱴᱟᱨᱱᱮᱴ ᱥᱮᱞᱮᱫ ᱟᱨ ᱡᱟᱦᱟᱭ ᱦᱮᱠᱟᱨ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱦᱮᱠᱟᱨ ᱥᱮ (Trojan Horse) ᱫᱟᱨᱟᱭ ᱥᱟᱢᱲᱟᱣᱼᱟ ᱟᱨ ᱥᱟᱹᱜᱤᱧ ᱠᱷᱚᱱ ᱟᱜ ᱥᱟᱢᱲᱟᱣ ᱛᱟᱞᱟᱛᱮ ᱡᱟᱦᱟᱭ ᱫᱟᱨᱟᱭ ᱛᱮ ᱱᱟᱱᱟ ᱦᱩᱱᱟᱹᱨ ᱜᱮᱭᱟᱱ ᱢᱩᱞᱚᱠ ᱠᱟᱹᱢᱤ ᱥᱚᱢᱵᱷᱚᱵ। ᱵᱚᱴᱱᱮᱰ ᱡᱚᱢᱵᱤ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱫᱟᱨᱟᱭ ᱛᱮ ᱯᱨᱟᱭ ᱱᱟᱱᱟ ᱦᱩᱱᱟᱹᱨ ᱥᱯᱟᱢ ᱤᱢᱮᱞ ᱠᱷᱚᱱ ᱟᱜ ᱮᱛᱚᱦᱚᱵ ᱠᱟᱛᱮ (DDoS) ᱦᱩᱞᱥᱟᱹᱭ ᱛᱟᱦᱮᱫ ᱠᱚ । ᱵᱤᱥᱤᱨ ᱵᱷᱟᱠ ᱠᱷᱮᱛᱨᱚ ᱨᱮ ᱡᱚᱢᱵᱤ ᱠᱚᱢᱯᱤᱭᱩᱴᱟᱨ ᱨᱮᱱᱟᱜ ᱱᱤᱡᱮ ᱜᱮ ᱥᱟᱲᱟ ᱥᱚᱵᱫᱚ ᱵᱟᱭ ᱧᱟᱢᱟ ᱩᱱᱤᱦᱟᱜ ᱥᱤᱥᱴᱮᱢ ᱡᱚᱢᱵᱤ ᱦᱤᱥᱟᱹᱵ ᱛᱮ ᱠᱟᱹᱢᱤ ᱛᱟᱦᱮᱫ। ᱡᱮᱦᱮᱛᱩ ᱢᱟᱞᱤᱠ ᱟᱜ ᱵᱟᱝ ᱜᱮᱭᱟᱱ ᱛᱮ ᱦᱩᱭᱩᱜᱼᱟ, ᱚᱱᱟ ᱠᱷᱟᱛᱤᱨ ᱨᱩᱯᱚᱠ ᱢᱮᱱᱮᱠ ᱢᱤᱫ ᱡᱚᱢᱵᱤ ᱥᱟᱶ ᱛᱩᱞᱟᱹ ᱡᱚᱠᱷᱟ ᱦᱩᱭ ᱟᱠᱟᱱᱟ । ᱟᱹᱰᱤ ᱜᱚᱴᱟᱝ ᱵᱚᱴᱱᱮᱰ ᱢᱤᱥᱤᱱ ᱢᱤᱫ ᱠᱟᱛᱮ ᱰᱮᱱᱟᱭᱤᱞ ᱚᱯ ᱥᱟᱨᱵᱷᱤᱥ ᱦᱚᱸ ᱡᱚᱢᱵᱤ ᱜᱟᱫᱮᱞ ᱥᱟᱶ ᱛᱩᱞᱟᱹ ᱡᱚᱠᱷᱟ ᱦᱩᱭᱩᱜᱼᱟ।